資訊洩露、成為黑客的攻擊跳板等等。而此漏洞主要針對 NETGEAR DGN-2200v1 設備並運行 v1.0.0.60 之前的 版本,而官方亦已於之後的更新中進行修復 (可參考官方公告)。
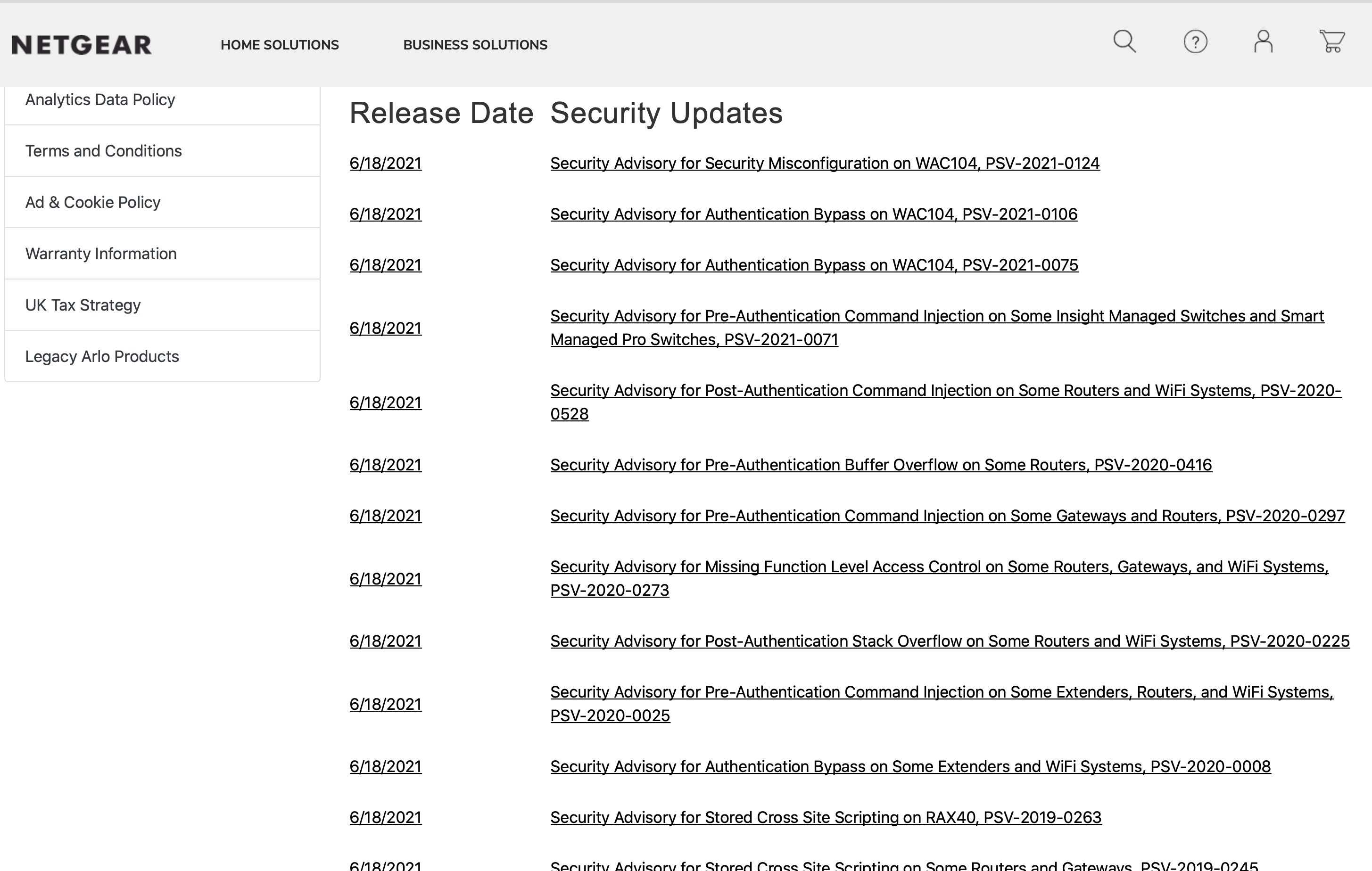
除了 DGN-2200v1 ,在 NETGEAR 官網 Security 頁面中,Netgear 在本年 6 月 18 日發出了多個安全性警示,當中包括修補了嚴重級別漏洞,例如 PSV-2020-0273,系統的存取控制存在漏洞,影響範圍包括 Gateways、Router 及 WiFi 產品。 CVSS v3 漏洞分數為「10」(滿分為10分),評級為「嚴重」。目前 NETGEAR 已針對上述安全漏洞發佈了修復程序,建議各位使用受影響 。
受影響設備型號
- D6220, running firmware versions prior to 1.0.0.48
- D6400, running firmware versions prior to 1.0.0.82
- D7000v2, running firmware versions prior to 1.0.0.52
- D7800, running firmware versions prior to 1.0.1.44
- D8500, running firmware versions prior to 1.0.3.43
- DC112A, running firmware versions prior to 1.0.0.40
- DGN2200v4, running firmware versions prior to 1.0.0.108
- RBK50, running firmware versions prior to 2.3.0.32
- RBR50, running firmware versions prior to 2.3.0.32
- RBS50, running firmware versions prior to 2.3.0.32
- RBK20, running firmware versions prior to 2.3.0.28
- RBR20, running firmware versions prior to 2.3.0.28
- RBS20, running firmware versions prior to 2.3.0.28
- RBK40, running firmware versions prior to 2.3.0.28
- RBR40, running firmware versions prior to 2.3.0.28
- RBS40, running firmware versions prior to 2.3.0.28
- R6020, running firmware versions prior to 1.0.0.34
- R6080, running firmware versions prior to 1.0.0.34
- R6120, running firmware versions prior to 1.0.0.44
- R6220, running firmware versions prior to 1.1.0.80
- R6230, running firmware versions prior to 1.1.0.80
- R6250, running firmware versions prior to 1.0.4.34
- R6260, running firmware versions prior to 1.1.0.40
- R6850, running firmware versions prior to 1.1.0.40
- R6350, running firmware versions prior to 1.1.0.40
- R6400v2, running firmware versions prior to 1.0.2.62
- R6700v3, running firmware versions prior to 1.0.2.62
- R6700v2, running firmware versions prior to 1.2.0.36
- R6800, running firmware versions prior to 1.2.0.36
- R6900v2, running firmware versions prior to 1.2.0.36
- R7000, running firmware versions prior to 1.0.9.34
- R6900P, running firmware versions prior to 1.3.1.44
- R7000P, running firmware versions prior to 1.3.1.44
- R7100LG, running firmware versions prior to 1.0.0.48
- R7200, running firmware versions prior to 1.2.0.48
- R7350, running firmware versions prior to 1.2.0.48
- R7400, running firmware versions prior to 1.2.0.48
- R7450, running firmware versions prior to 1.2.0.36
- AC2100, running firmware versions prior to 1.2.0.36
- AC2400, running firmware versions prior to 1.2.0.36
- AC2600, running firmware versions prior to 1.2.0.36
- R7500v2, running firmware versions prior to 1.0.3.38
- R7800, running firmware versions prior to 1.0.2.58
- R7900, running firmware versions prior to 1.0.3.8
- R7960P, running firmware versions prior to 1.4.1.44
- R8000, running firmware versions prior to 1.0.4.28
- R7900P, running firmware versions prior to 1.4.1.30
- R8000P, running firmware versions prior to 1.4.1.30
- R8900, running firmware versions prior to 1.0.4.2
- R9000, running firmware versions prior to 1.0.4.2
- RAX120, running firmware versions prior to 1.0.0.74
- RBK752, running firmware versions prior to 3.2.16.6
- RBR750, running firmware versions prior to 3.2.16.6
- RBS750, running firmware versions prior to 3.2.16.6
- RBK852, running firmware versions prior to 3.2.16.6
- RBR850, running firmware versions prior to 3.2.16.6
- RBS850, running firmware versions prior to 3.2.16.6
- WNR3500Lv2, running firmware versions prior to 1.2.0.56
- XR450, running firmware versions prior to 2.3.2.32
- XR500, running firmware versions prior to 2.3.2.32
另外 NETGEAR 亦發佈了另一個對於驗證前指令注入 (pre-authentication command injection) 的高危險漏洞 (PSV-2019-0151),CVSS v3 漏洞分數為「9.6」、評級為「嚴重」。而相關的修復程序已發佈,NETGEAR 官方強烈建議盡快下載最新的 Firmware 進行修復 (可參考官方公告)。
受影響設備型號
- RBK40, running firmware versions prior to 2.5.1.16
- RBR40, running firmware versions prior to 2.5.1.16
- RBS40, running firmware versions prior to 2.5.1.16
- RBK20, running firmware versions prior to 2.5.1.16
- RBR20, running firmware versions prior to 2.5.1.16
- RBS20, running firmware versions prior to 2.5.1.16
- RBK50, running firmware versions prior to 2.5.1.16
- RBR50, running firmware versions prior to 2.5.1.16
- RBS50, running firmware versions prior to 2.5.1.16
- RBS50Y, running firmware versions prior to 2.6.1.40
盡管現今的網絡產品的保安措施及技術不斷提升,然而黑客的入侵手法愈來愈高明,亦會持續去發堀更多漏洞及未有及時修補的裝置,因此使用者必須保持設備的系統於最新狀態,及適當地開啟產品的保安防護設定,以降低被入侵的風險。